A paper published by security researchers at the Technical University of Berlin reveals that AMD’s firmware-based Trusted Platform Module (fTPM / TPM) can be fully compromised, thus allowing full access to the cryptographic data held inside the fTPM in an attack called ‘faulTPM.’ The attacker needs physical access to the device to exploit the vulnerability.
The paper is here: https://arxiv.org/abs/2304.14717
The researcher also shared the code used: https://github.com/PSPReverse/ftpm_attack
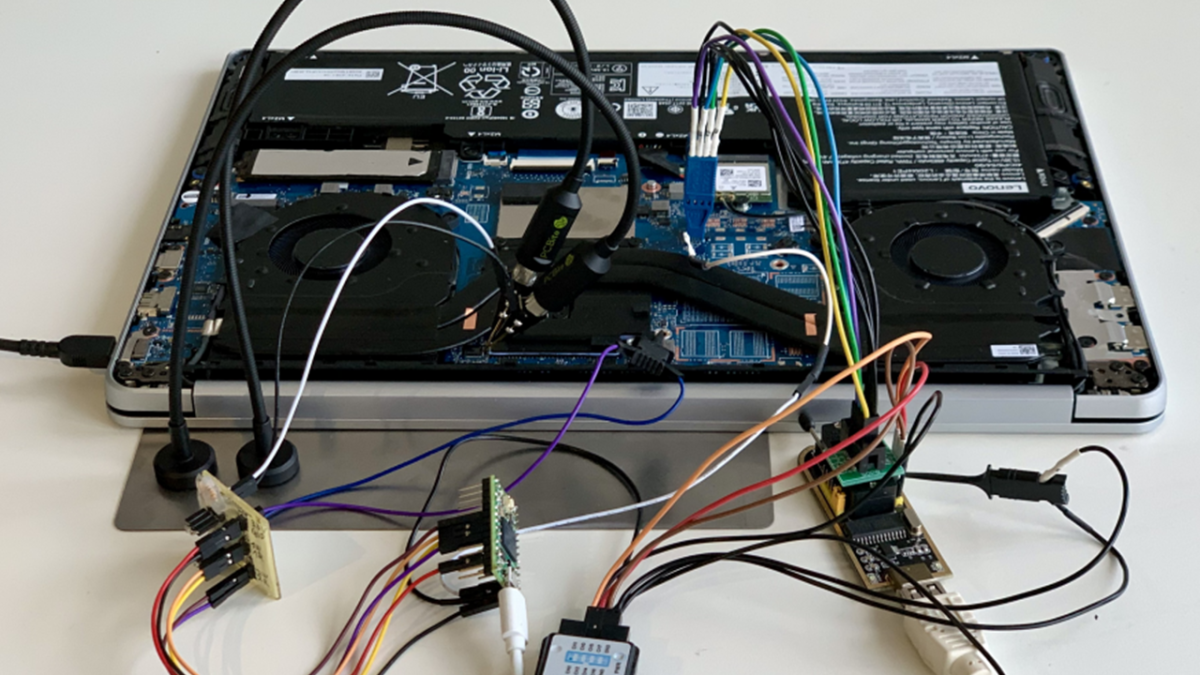


I am no expert, but I believe the problem is that TPM+Bitlocker lets users use a short PIN (6 numbers) to protect their drive. The idea is the TPM module will hardware lock itself after a certain number of failed attempts. However by compromising the TPM module itself, this short PIN can be easily brute-forced.
It’s worse than that since the pin is optional. So in most case there’s no pin set. In which case the TPM is the only thing protecting the disk encryption key.